Vault¶
![]() Vault by HashiCorp is an open source tool to manage secrets and protect sensitive data. A secret is anything that you want to tightly control access to, such as API
keys, passwords, or certificates.
Vault by HashiCorp is an open source tool to manage secrets and protect sensitive data. A secret is anything that you want to tightly control access to, such as API
keys, passwords, or certificates.
The Vault approach is designed for dynamic infrastructures where the network perimeter is not known (e.g. multi-cloud) and relies on identity-based security.
Note
In this tutorial, please replace the following values:
ZONE_NAMEwith the name of the administrative zone (it starts withocb-)CLUSTER_NAMEwith the name of the Kubernetes® cluster provisioned by Caascad
Introduction¶
Vault provides different means to manage sensitive information for your applications and infrastructure. Secrets are stored in an encrypted data store and can be retrieved via a REST API.
-
Different methods of authentication and secrets management are possible depending on use cases.
-
The access to secrets is controlled by policies which can be linked to identities (operators, applications). The policies can allow or deny access to parts of the Vault API.
-
The most used API is the "KV store secrets engine" which allow to store arbitrary secret data in Vault. Its usage is described in the next section.
-
In Caascad, users can log in Vault with an OIDC backend (Keycloak) like other Caascad applications. Depending on your Keycloak roles you will have more or less access to the Vault API.
Vault access¶
In your administration environment, Vault service is located at this address:
https://vault.ZONE_NAME.caascad.com
Available roles¶
The global roles caascad-devops and caascad-devops-<CLUSTER_NAME> allow operators
to access Vault and to manage Concourse CI secrets and secrets for Kubernetes® applications.
Login¶
To be able to login into Vault, you need to use your Keycloak credentials. For more info regarding Keycloak, please refer to Authentication page.
WebUI¶
- Choose the
OIDCmethod in the dropdown list - Click on the "Sign in with OIDC Provider" button
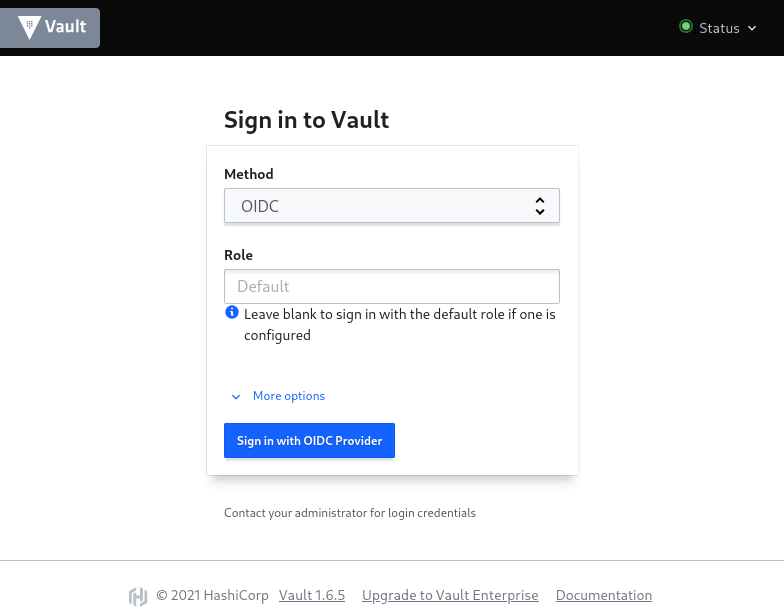
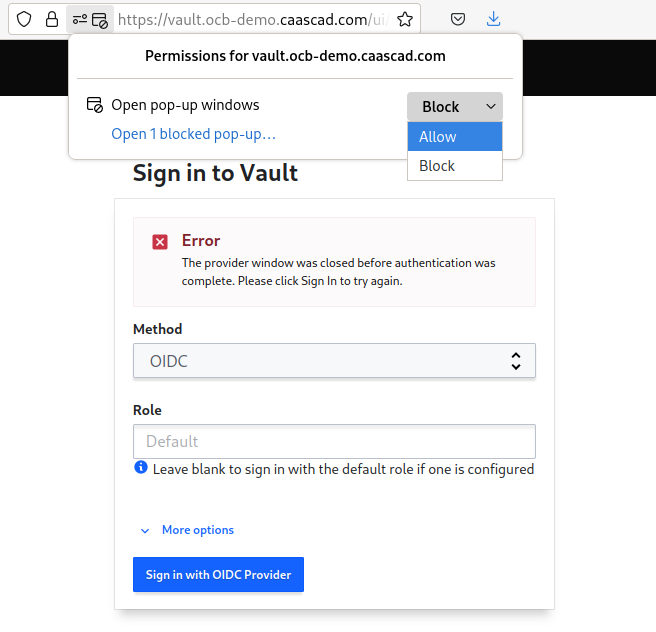
- A popup window should appear to login. If your browser blocks this popup the first time, you need to allow popups for this website and click again on "Sign in with OIDC Provider".
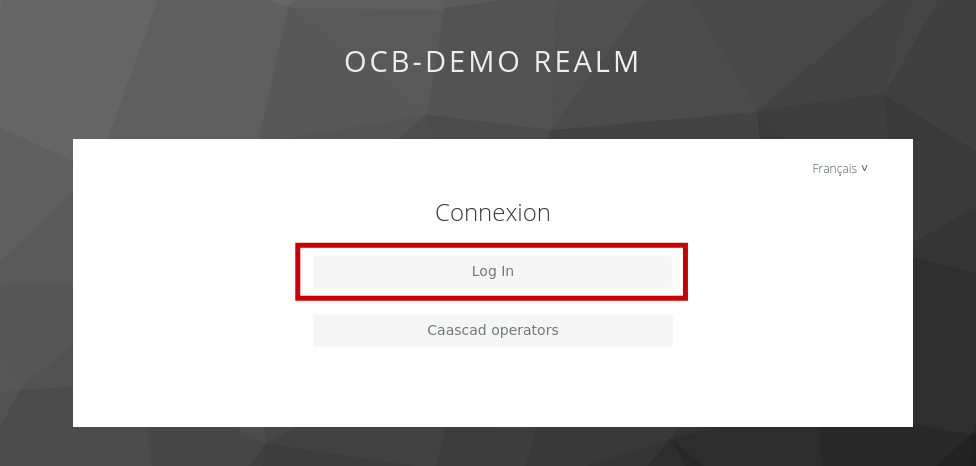
- The popup will show the Keycloak login page. Click on "Log In"
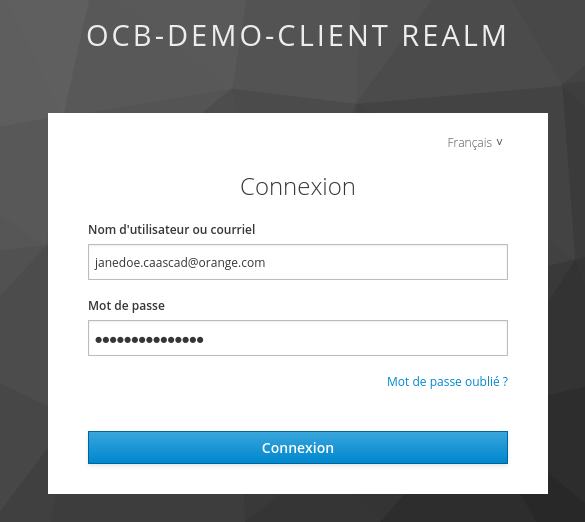
- Then enter your user / password
CLI¶
You can get the vault binary for your OS at https://www.vaultproject.io/downloads.
To login with the CLI:
export VAULT_ADDR=https://vault.ZONE_NAME.caascad.com
vault login -method=oidc
This will open a login page in your browser. Once logged in, you can close the page and get back to the console.
You should see an output like this one:
$ vault login -method=oidc
Complete the login via your OIDC provider. Launching browser to:
https://keycloak.ocb-demo.caascad.com/auth/realms/ocb-test01/protocol/openid-connect/auth?client_id=vault&nonce=739b2167e4c0d71a60ef3878c9aa31566497361e&redirect_uri=http%3A%2F%2Flocalhost%3A8250%2Foidc%2Fcallback&response_type=code&scope=openid&state=d1629b03a05e515beb774f4d0f108b59404dc55d
Success! You are now authenticated. The token information displayed below is already stored in the token helper. You do NOT need to run "vault login" again. Future Vault requests will automatically use this token.
Key Value
--- -----
token XXXXXXXXXXX
token_accessor Sb9s3OJXBiCpFzFLP3JKC2n1
token_duration 168h
token_renewable true
token_policies ["default"]
identity_policies ["caascad-concourse-member"]
policies ["caascad-concourse-member"]
token_meta_role caascad
This has retrieved and stored a token to access Vault with the CLI. In this example the token will expire in 168h. Once it has expired repeat the same procedure to retrieve a new token.
To display the authenticated token information :
$ vault token lookup
You will get the expiration date of your token.