Clair : vulnerability analysis¶
![]() Clair is used for the static analysis of vulnerabilities in application containers.
Clair is used for the static analysis of vulnerabilities in application containers.
It is fully integrated to Quay. Every time an image is pushed in your Docker registries, Clair will scan each layer of the image to find possible vulnerabilities.
Note
In this tutorial, please replace the following values:
ZONE_NAMEwith the name of the administrative zone (it starts withocb-).
Source of vulnerabilities¶
Clair scans are based on the Common Vulnerabilities and Exposures database (CVE) and similar databases from Red Hat, Ubuntu, Debian, etc..
Here are all the data sources :
- Debian Security Bug Tracker
- Ubuntu CVE Tracker
- Red Hat Security Data
- Oracle Linux Security Data
- Amazon Linux Security Advisories
- Alpine SecDB
- NIST NVD
How Clair works¶
- Every 6 hours, Clair checks the data sources and imports newly found vulnerabilities into its own database.
- Quay uses Clair API for indexing every image, generating a list of installed packages. This list is stored in Clair database.
- Quay uses Clair API to query Clair database and correlates any installed package (of any docker image) with the vulnerabilities found in data sources
As every Docker image is systematically indexed, Clair doesn't need to re-scan it when when new vulnerabilities are found, it already knows which packages are installed in each of them, and can notify as soon as a new vulnerability is found.
Vulnerability scans and results¶
Once an image is pushed into the registry, Clair is automatically notified to scan it. The scan can take a while depending on the size and the number of layers of the image.
Here is an example of a new image about to be scanned:
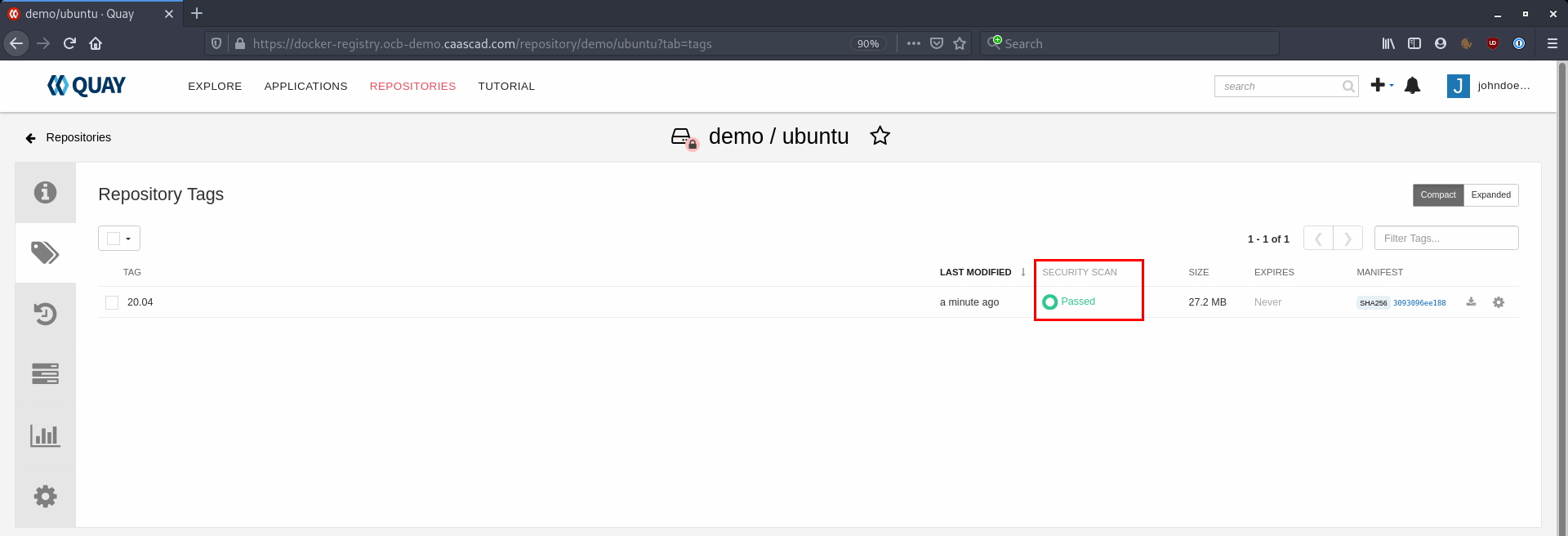
As soon as an image has been scanned, Clair notifies for vulnerabilities, if it can't find any, the status "Passed" is displayed. Here is an example of a scanned image with no vulnerability:
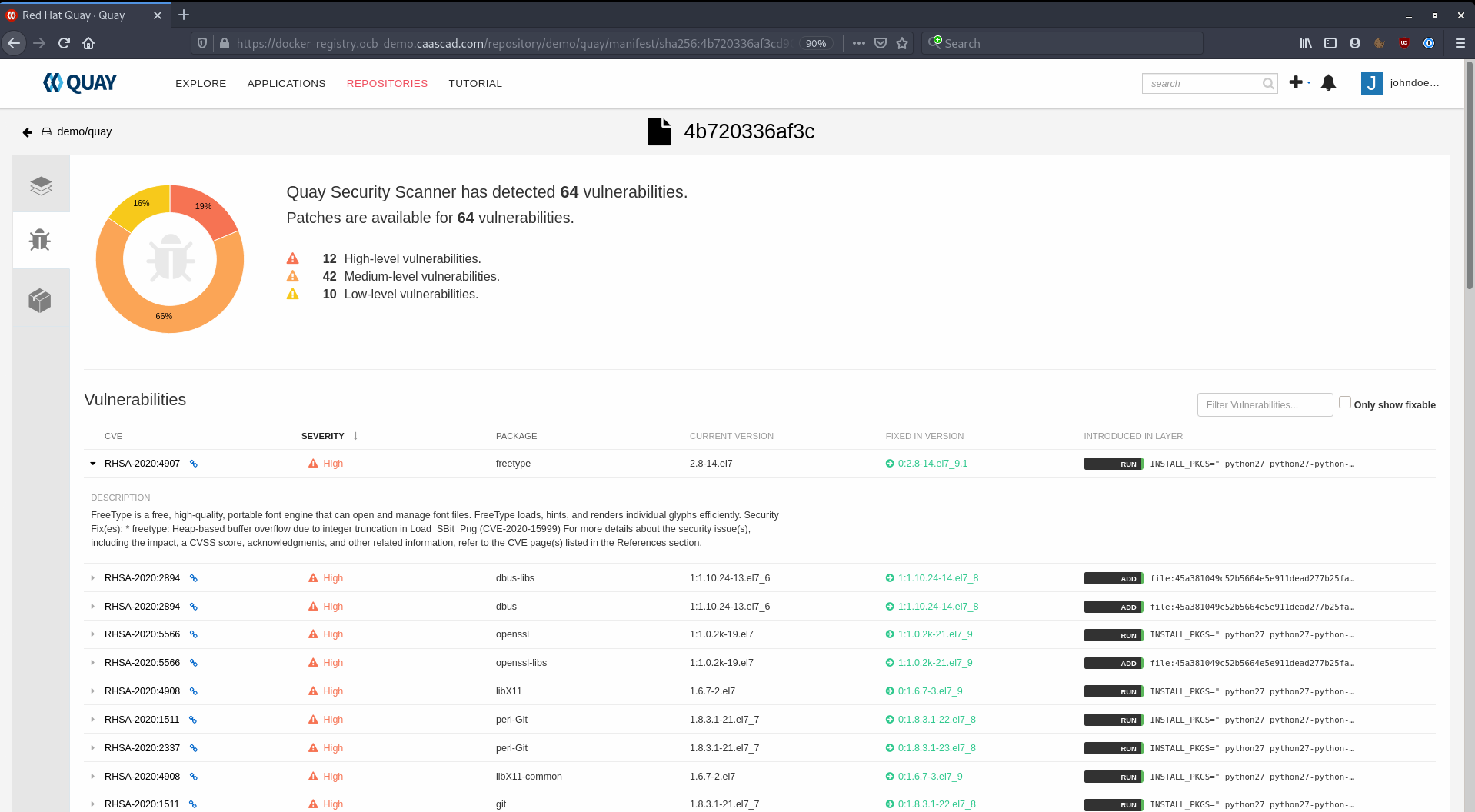
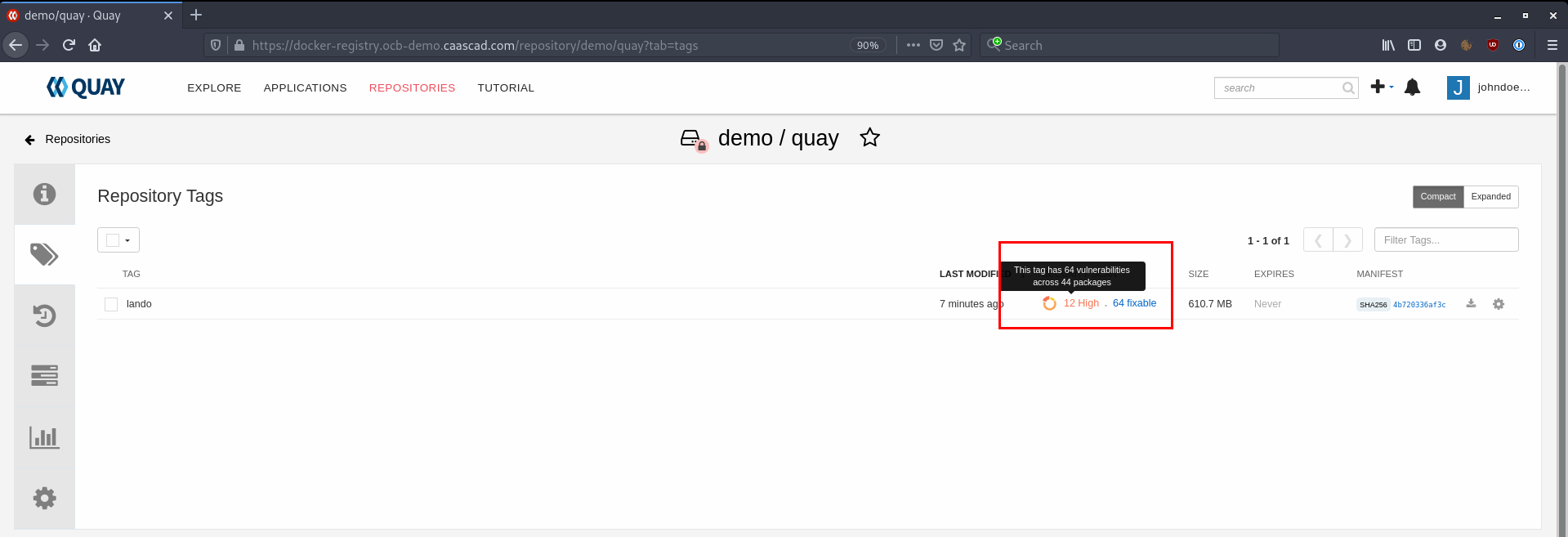
Here is an example of a scanned image with 64 vulnerabilities, with 12 considered as High-Level.
If you click on it, Clair gives you more details about all of those vulnerabilities, and how you can fix them. For each vulnerability found, Clair displays:
- CVE and its description
- severity
- vulnerable system package and package version
- what system package version could fix the vulnerable one